The new Ubuntu Version “Hardy Heron” featuring Long Term Support (LTS) has gone beta and will be released in about a month.
Nagios 3.0 released
Nagios, which was voted 2007 Monitoring Application of the Year by LinuxQuestions.org has been released as 3.0 Stable.
Goolag Scanner goes fishin
Storing ..um.. classified Information on your webserver in hidden directories is not exactly very bright because you can be sure that google will index anything it can get.
The goolag scanner, which was recently released by the famous hacker group cultDeadcow actually found pornography on chinese government owned (gov.cn) sites and security holes on western servers.
http://www.cultdeadcow.com/archives/2008/03/cult_of_the_dead_cow.php3
Please assume that files being stored in http://mydomain.com/_this/is/a_super/secret/directory/ will easily be found by simple methods such as specially designed search queries:
intitle:index.of +”last modified” +”parent directory” +(pdf|doc) +”Secret” -htm -html -php -asp
Attacks on disk encryption keys
A Princeton computer scientist team has released a white paper which documents their cold boot attacks on encryption keys. The scenarios are based on a key recovery involving primarily laptop computers using various methods to keep the key stored in dram on a power off.
Very interesting article and a guideline on preventing attacks like this. The most effective way is certainly limiting boot options in order do prevent anyone booting up tools to steal your encryption key.
http://citp.princeton.edu.nyud.net/pub/coldboot.pdf
SecuriTeam Article
Internet Nostalgia
This is how information was exchanged in on the net in the old bbs days. Textfiles.com Includes some really old stuff from the beginning of the private internet use.
Textfiles.com file directory
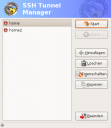
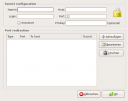
Gnome SSH Tunnel Manager
If you use encrypted ssh tunnels a lot you may find this tool pretty interesting.
Gstm is a fully functional gui for managing all your ssh tunnels and redirects.I really like this on the EEE PC because it saves a lot of keyboard interaction.
A simple apt-get install gstm will immediately install the software package, providing you have the correct repositories.
Debian 3.1/Sarge Security Support terminated
I highly reccomend anyone still running Sarge to start planning on an upgrade to Etch, the current stable release.