Since i will be replacing my laptop pretty soon i am currently looking for a worthy successor for my old Acer Aspire. Critical Factors this time are CPU Power and Hardware Virtual Machine Support (such as Intel VT in the current Core 2 Duo models) and mobile battery life.
I dont really care about the host system since that will not drain the resources from the hardware ( but be sure, the virtual machine lab will 🙂 )
Currently still in the battle are a Lenovo Thinkpad R60 and a Macbook 2,2 ghz (black) which are about the same price (where the Thinpad has a 3D card and the MacBook a bigger Hard Drive)
On the other hand, i might consider getting an Inspiron 6400 from Dell with Ubuntu preinstalled.
I have had quite some experience now with Thinkpads from the field, solidness, data security and well… several small issues that can drive me crazy.
As a testing platform i performed a Ubuntu Gutsy Gibbon 7.10 Horde 5 install which will be going final a few weeks.
Setting up the system was as always quite easy and the first boot revealed that practically all hardware components were working (didn’t try out the fingerprint scanner yet).
Sound was no problem although the default System Beep is very annoying. Lan and WLAN connection worked instantly and will connecting you out of the box if you are connecting to a dhcp device.
The proprietary drivers for the wireless Intel 3945 network card were installed as for the other restricted driver devices (gpio and ATI radeon card) were waiting to be enabled.
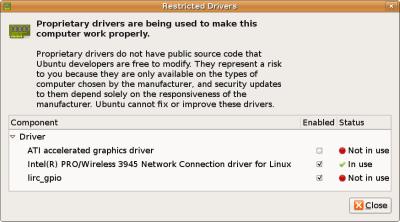
The system correctly installed an smp kernel and load balancing seems to be working fine.
Some of the hardware keys were running (try playing with the thinpad-keys packet) such as the volume control and the screen brightness. So after just 30 minutes, i hade a fully operable system with essentials like an office suite (OpenOffice) email applications (Evolution) and a Webbrowser (Firefox 2.0.0.6) running.
So far no drivers required to be installed yet 🙂
The performance test was done overall with beryl and compiz and running pretty smooth with the onboard 3d card.

