English Language
German Language

technology | art | nature
all about networking
English Language
German Language
https://www.youtube.com/watch?v=LB53L6IKA_Y
On the journey to CCNA Security (210-260)
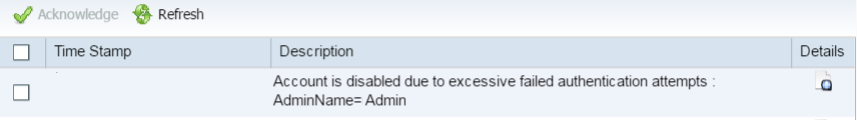
Correlating Log files are an important aspect when responding to incidents/attacks/outages regarding your Cisco devices.
However I have noticed for a while that my logging timestamps are off an hour from the actual clock synced by NTP.
After some digging I realized that Cisco devices use
service timestamps log datetime
as a default. You can check the default values using the command:
sh run all | inc timestamp
In order for your logs to use the local clock time you need to issue the command
device(config)# service timestamp log datetime localtime
From now on, your logging timestamp should be identical to your local time on the device.
Great PBS documentary on the NSA surveillance “program”
Part 1 mainly focuses on the NSA program post 9/11 and the events that lead people like Thomas Drake, William Binney and Edward Snowden to blow the whistle.
Part 2 covers the ties between the US government and Data Mining companies like Google, Facebook and Apple.
The CCNA training videos from this Kickstarter Project are now available.
Internet censorship is bad – especially when it is abused to censor media reports about potentially corrupt government officials. Luckily a lot of incompetent people try to implement censorship via DNS.
Censorship via DNS is a method which is pretty easy to bypass and some people have responded to this this:
http://mashable.com/2014/03/21/twitter-ban-turkey-graffiti/?utm_medium=feed&utm_source=rss
And no, I will not go into detail here on how to do it right – for obvious reasons….
Managing Access Lists on Cisco IOS devices can be a real headache. Copying ACLs and Editing them in a Text Editor was a widely spread method until extended ACLs implemented Named Access Lists (nacls) with featured sequence numbers.
Extended IP access list my_acl_in 2 permit icmp ..... (1234 matches) 3 permit ip any host x.x.x.x 10 permit ip .... 11 permit ip .... 12 permit ip .... 13 permit ip .... 14 permit tcp any host ...... eq 443 15 permit tcp any host ...... eq www
Btw. the IPv6 Access list sequence numbers are placed at the end
permit tcp host 2001:DB8:1::32 host 2001:DB8:2::32 eq ssh sequence 1
Sequence Numbers allow for quick changes to an ACL without the copy&paste foo. A growing and ever changing ACL however can post a challange to your sequencing once the gaps are filled. In order to realign your Access Control Entries you can use the resequence command to put your ACEs in order again.
r1(config)#ip access-list resequence ? <1-99> Standard IP access-list number <100-199> Extended IP access-list number <1300-1999> Standard IP access-list number (expanded range) <2000-2699> Extended IP access list number (expanded range) WORD Access-list name r1(config)#ip access-list resequence my_acl_in ? <1-2147483647> Starting Sequence Number r1(config)#ip access-list resequence my_acl_in 5 ? <1-2147483647> Step to increment the sequence number r1(config)#ip access-list resequence my_acl_in 5 5
will resequence your ACEs to look something like this:
Extended IP access list my_acl_in 5 permit icmp ..... (1234 matches) 10 permit ip any host x.x.x.x 15 permit ip .... 20 permit ip .... 25 permit ip .... 30 permit ip .... 35 permit tcp any host ...... eq 443 40 permit tcp any host ...... eq www
This feature will definitely help to keep your sanity.
I find it quite a bit strange that this fuction is not mentioned on neither the 640-802 CCNA nor the 640-554 CCNA Security Cert Guides.
For more infos, check out the Cisco ACL sequence numbering guide